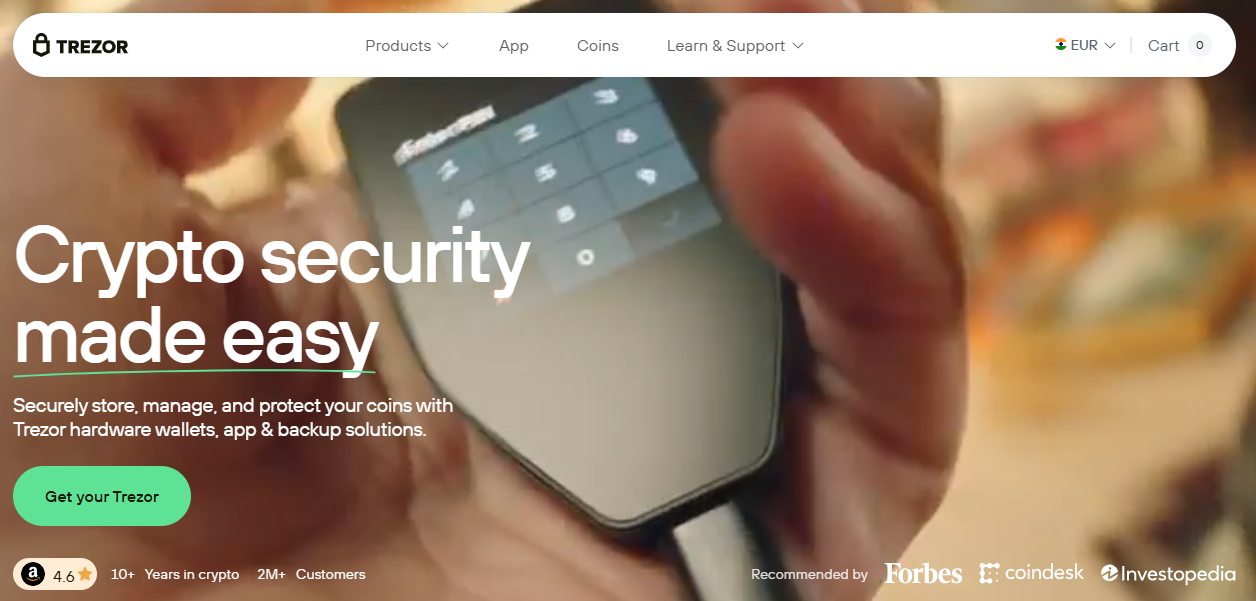
Trezor Login – Secure Your Crypto with Confidence
Experience smooth, secure, and seamless access to your digital assets. Trezor Login offers hardware-level protection wrapped in a beautifully designed interface for the modern crypto user.
Hardware-Backed Security
Your private keys never leave your device. Each login request is authenticated directly on your Trezor hardware wallet, ensuring full protection from phishing, malware, or online intrusion attempts.
User-Centric Experience
With Trezor Login, security doesn’t come at the cost of usability. The interface is intuitive, responsive, and supports multiple platforms for convenient crypto access.
Decentralized Control
Trezor keeps your crypto journey transparent and autonomous. No cloud storage, no central authority — just direct, local ownership of your keys and funds.
How to Use Trezor Login – Step-by-Step Guide
- Step 1: Go to Trezor.io/start. This is the official and secure entry point to begin setting up your device and logging in.
- Step 2: Connect your Trezor device to your computer. Allow the browser to detect your hardware wallet via USB connection.
- Step 3: Launch Trezor Suite or select the web version. Click “Login with Trezor” and confirm the session on your device screen.
- Step 4: Access your dashboard to manage your portfolio — from Bitcoin and Ethereum to DeFi tokens — with complete visibility and security.
Trezor Login – Features that Define Safety
🔐 Multi-Layer Authentication
Every login confirmation happens on your hardware device, separated from your connected system for maximum defense.
🌍 Cross-Platform Sync
Access your Trezor account via desktop or web, with identical security integrity maintained across all platforms.
💡 Intuitive Dashboard
Get a real-time overview of your holdings, price trends, and transaction history — all within a sleek visual interface.
🪙 Multi-Asset Management
Control multiple cryptocurrencies and tokens in one unified dashboard. Trezor supports Bitcoin, Ethereum, XRP, ADA, and more.
Why Trezor Login Is Safer Than Password-Based Systems
| Feature | Trezor Login | Traditional Login |
|---|---|---|
| Private Key Storage | Offline, hardware-secured | Online, vulnerable to leaks |
| Data Privacy | No personal data stored | User credentials stored on servers |
| Phishing Resistance | Hardware confirmation required | Vulnerable to fake sites |
| Recovery Method | Seed phrase backup | Email/password reset |
FAQs – All About Trezor Login
No. Every session requires device confirmation to ensure security and authenticity.
It works seamlessly with Chrome, Firefox, Brave, and Edge through WebUSB or Trezor Bridge.
Yes. Even if your network is compromised, your hardware wallet isolates your keys from online threats.
Your recovery seed restores full access. Keep it offline and never share it digitally.
“With Trezor Login, your crypto isn’t just protected — it’s empowered. You hold the keys, you hold the future.”
Whether you’re managing Bitcoin or exploring the expanding DeFi universe, Trezor Login ensures your journey begins with trust, transparency, and total control.